- 21 Mar 2024
- Drucken
Security
- Aktualisiert am 21 Mar 2024
- Drucken
Security
In the "Security" tab, you can decide who can access a Webcast in the WebcastConsumer.
You can allow access:
only to browsers connecting with certain external IP addresses
only to browsers referred by link to the Webcast from certain domains
only to viewers with specific email addresses or domains
only to viewers who enter a pre-defined access code
using a HMAC token.
You can configure combinations of these options, in which case all sets of conditions must be satisfied before access is granted: the IP range is checked first, then the referrer domain, then the password and finally the registered email address.
If configured for your account, you can also enable or disable Peer-to-Peer video distribution. When enabled, the live video traffic is distributed within your network, reducing pressure on your company's external network bandwidth.
SSO Groups
For SSO groups, you can use wildcard group names (indicated by the * symbol).
To permit access to SSO groups, you can add either a full name such as "Marketing" and "Management," or a wildcard such as "Ma*" for SSO groups.
Note that the wildcard implies any group starting with "Ma." Therefore, you should not enter the wildcard at the beginning or in the middle such as Ma or Ma.
Use wildcard email addresses (indicated by *) to catch any email address starting with the specified characters.
For example, Ma* will catch Mary@example.com and Mark@example.com.
SSO permitted email addresses
In addition to permitting access to SSO groups, you can now add SSO-permitted e-mail addresses.
Specifically, this enables individual employees to log into Webcast Consumer using their SSO IDs.
Use wildcard email addresses (indicated by *) to catch any email address starting with the specified characters.
SSO Permitted UUIDs
Add permitted UUIDs to Webcast Manager to enable employees to sign in using SSO based on their internal UUIDs.
Bulk import of SSO permitted attributes
You can import multiple SSO-permitted email addresses or UUIDs by uploading a comma-separated-values file containing entries for either SSO emails or UUIDs.
The input is then validated, and the imported entries are shown, along with those that were excluded. Invalid entries might be email addresses with empty spaces or typos.
If you want to correct invalid entries, you can download the list of excluded entries to correct them and re-import it.
You can also remove the complete list of entries, including both successfully imported entries and excluded entries.
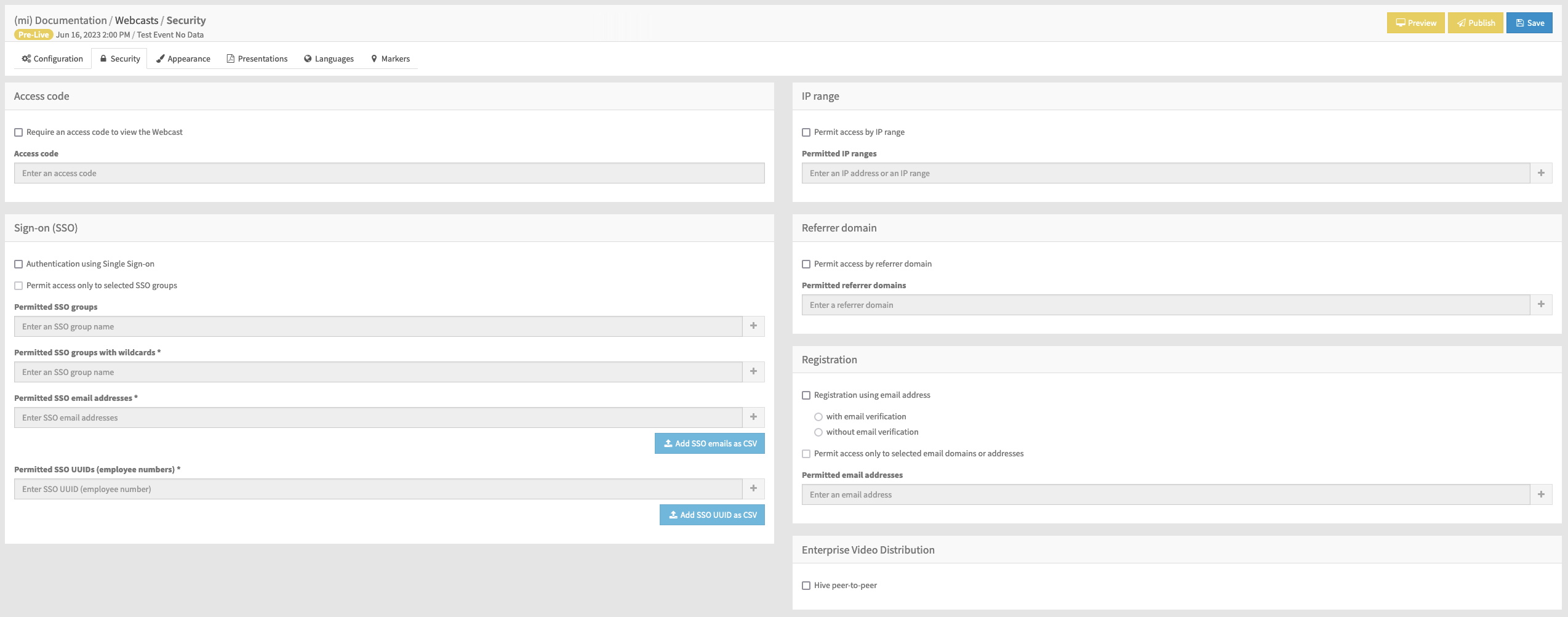
IP Range
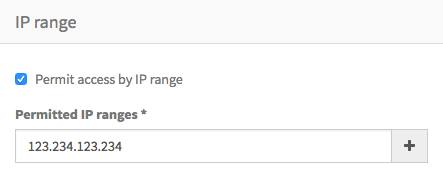
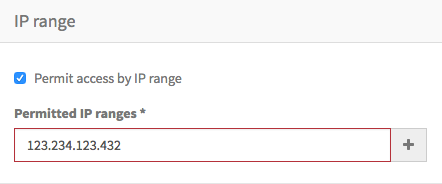
To permit access only to browsers from specific IP addresses or ranges, check the option Permit access by IP range. Then, you can enter either a single IPv4 address in the format 123.234.123.234, or an IPv4 range in the format 123.234.123.234/24. This second format is known as CIDR notation and is a short form of including a whole subnet of addresses. More information on the CIDR notation is available here: Classless Inter-Domain Routing.
The IP address that the WebcastConsumer receives from a client is most likely not the same as the client's local or internal IP address. Be sure to use the external IP address or range when adding entries to this list.
To see what the external IP address is, simply type "what's my IP?" into a search engine.
The value entered is validated, and if valid the + button is enabled to add it to the permitted list. Invalid entries will be highlighted with a red border.
You can add as many IP addresses or ranges as you wish. It is not possible to add the same value more that once. Each entry is shown beneath the entry field, and can be deleted using the✖️ within the label.
Remember to Save your entries before switching to a different tab.
If you later uncheck the Permit access by IP range option, any entries made are retained but are not used to manage access to the Webcast. You can later recheck the option without re-entering the IP entries.
Referrer Domain
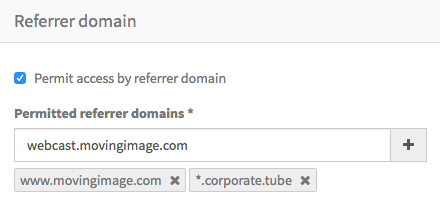
To permit access only to browsers referred from specific domains, check the option Permit access by referrer domain. Then, you can add either a fully-qualified domain such as www.movingimage.com, or a wildcard domain such as .movingimage.com. In the second case, note that the wildcard . implies any subdomain of movingimage.com. You should not enter the protocol http:// or https://
The value entered is validated, and if valid the + button is enabled to add it to the permitted list. Invalid entries will be highlighted with a red border.
You can add as many referrer domains as you wish. It is not possible to add the same value more that once. Each entry is shown beneath the entry field, and can be deleted using the ✖️ within the label.
Remember to Save your entries before switching to a different tab.
If you later uncheck the Permit access by referrer domain option, any entries made are retained but are not used to manage access to the Webcast. You can later recheck the option without re-entering the referrer domain entries.
Sign-on and Registration
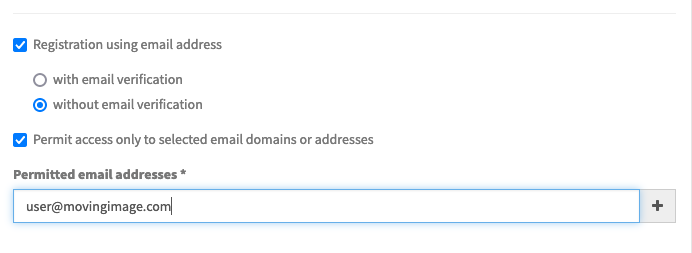
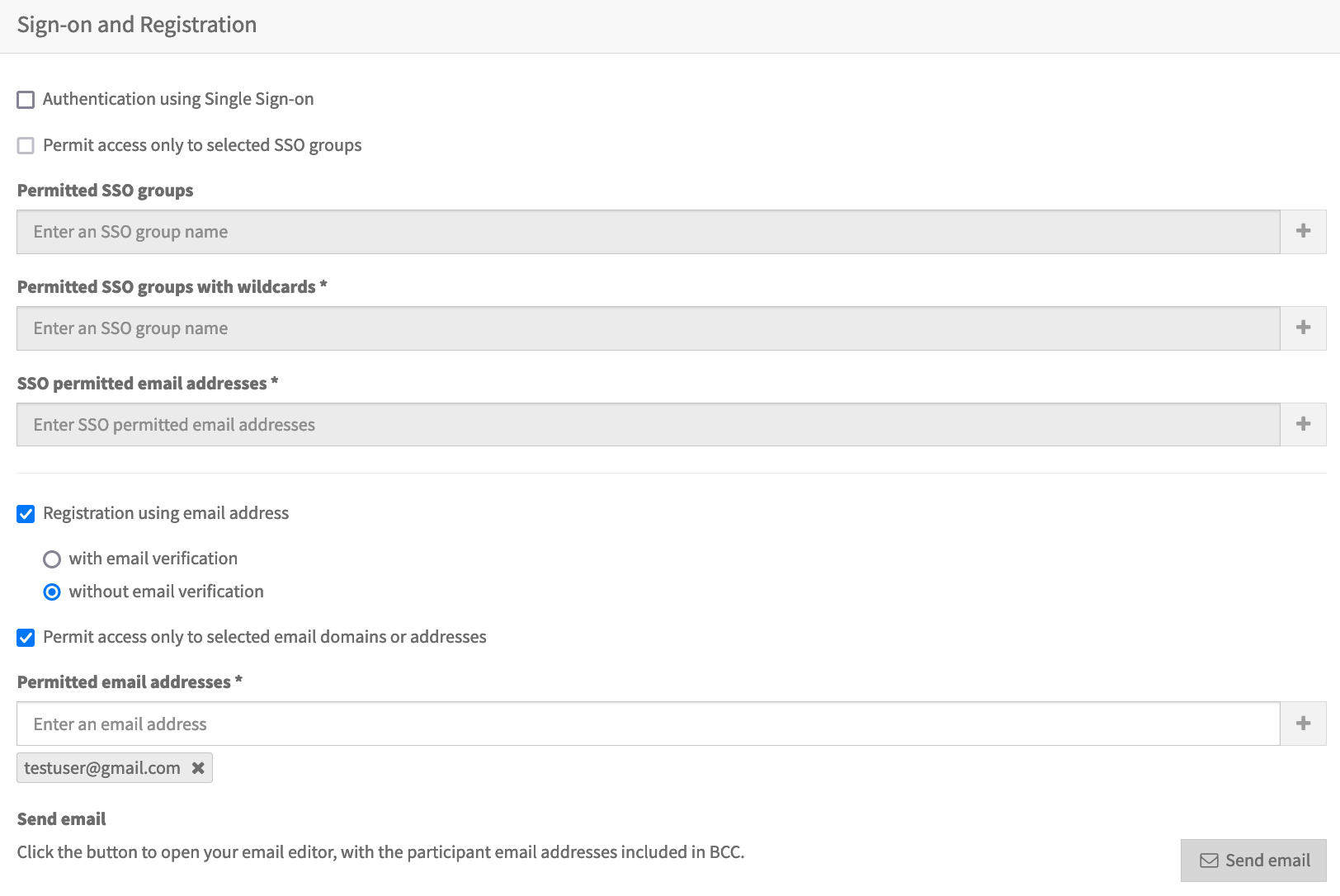
To require viewers to enter registration information, check the option Registration using email address. Viewers accessing the Webcast will then be required to complete a simple registration form before accessing the Webcast.
If your company operates within the European Union, or anticipates the collection of registration data from viewers in the European Union, the EU General Data Protection Regulations may apply. It is recommended to configure a connection to your company privacy policy under the Customer menu option. Contact movingimage Professional Services if you need assistance.
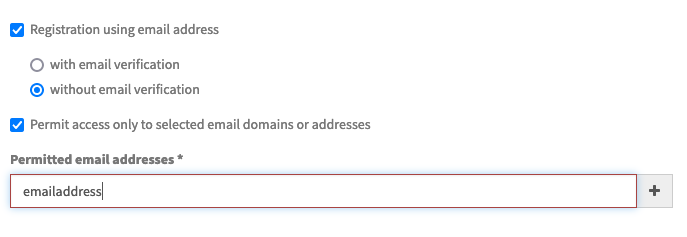
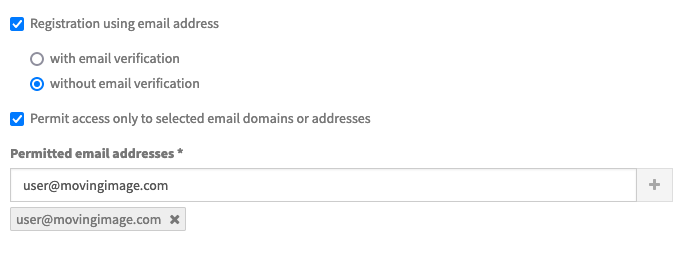
To permit access only to viewers registering with specific email addresses, additionally check the option Permit access only to selected email domains or addresses. Then, you can add either individual email addresses such as john.doe@movingimage.com, or a wildcard email domain such as @movingimage.com. In the second case, note that the wildcard @ implies any email address of movingimage.com.
The value entered is validated, and if valid, the + button is enabled to add it to the permitted list. Invalid entries will be highlighted with a red border.
You can add as many email addresses or domains as you wish. It is not possible to add the same value more that once. Each entry is shown beneath the entry field, and can be deleted using the ✖️ within the label.
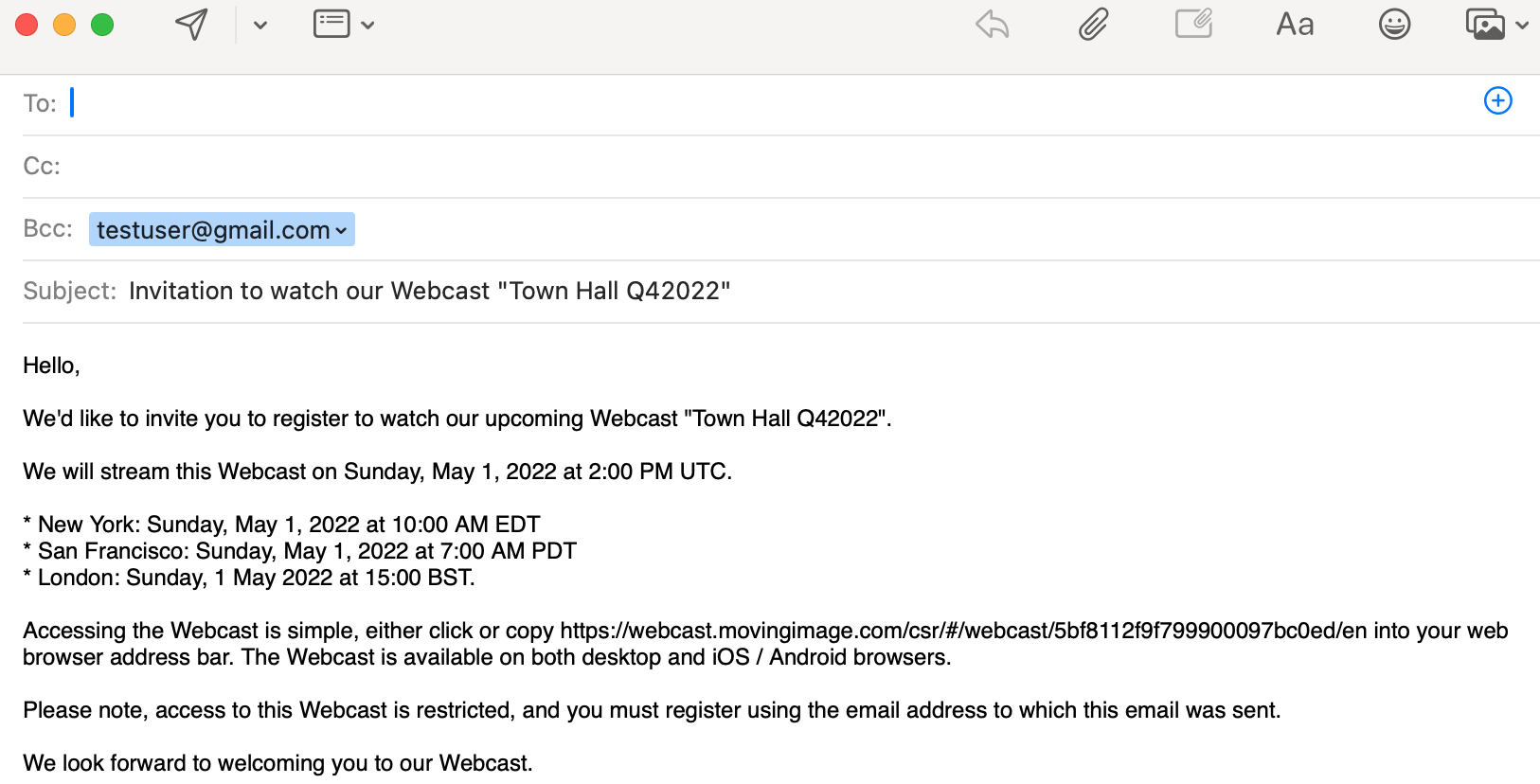
After saving your changes, click Send email. An email message will open in your default email editor with the participant email addresses in the Bcc field and a pre-written message.
Remember to Save your entries before switching to a different tab.
If you later uncheck the Permit access only to selected email domains or addresses option, any entries made are retained but are not used to manage access to the Webcast. You can later recheck the option without re-entering the email address entries.
Access code
To permit access only to viewers who enter a predefined access code, check the option Require an access code to view the Webcast. Then, enter your desired code in the Access Code field.
Enterprise Video Distribution
This option toggles the use of Peer-to-Peer live streaming within your company's intranet.
This is a separately bookable feature for the Webcast package, and requires that your internal network uses one of the following Peer-to-Peer technologies:
Hive (using a Java client)
Hive (using WebRTC)
Kollective
HMAC token authorization
The HMAC token is generated client-side and follows a specific standard. Please contact your administrator for more information about implementation used by your organization.
This security feature ensures that only authorized users are able to access a protected Webcast.
Specifically, this feature verifies if the HMAC token provided by the viewer is valid.
Speak to your Account Manager for further details.
.png)